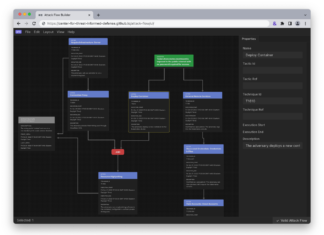
Mapping the Thales Satellite Hacking Demo using SPARTA TTPs and PWNSAT ATT&CK Flow Builder...
In 2023, during the CYSAT conference, Thales presented a live demonstration of a satellite hacking scenario, a milestone event that shed light on the...
2nd International Conference on Gravitation, Astrophysics and Cosmology (ICGAC2026) – April 16-18, 2026 in...
We are pleased to announce that the 2nd International Conference on Gravitation, Astrophysics and Cosmology (ICGAC2026) will be held on April 16-18, 2026, in...
Two big announcements : the release of SPARTA v3.1 with MITRE’s EMB3D mapping and...
In the following article, discover the major advancements announced with the release of SPARTA v3.1: the addition of new NIST space segment guidance, the...
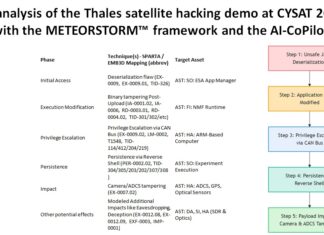
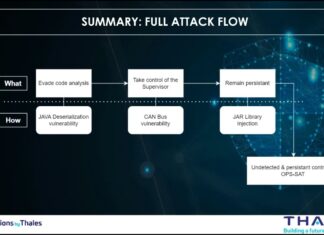
An analysis of the Thales satellite hacking demo at CYSAT 2023 with the METEORSTORM™...
Disclaimer
Please be informed that the analysis detailed in this article is entirely separate from the hacking experiment conducted by the Thales team on the...
Exploring the power of the METEORSTORM™ framework — a framework built for full-spectrum modeling...
I'm very proud to have successfully taken up a new challenge exam in beta version about METEORSTORM™ framework which allowed me to obtain the...
An analysis of the Thales satellite hacking demo at CYSAT 2023 with the MITRE...
Disclaimer
Please be informed that the analysis detailed in this article is entirely separate from the hacking experiment conducted by the Thales team on the...
Enhancing Threat Understanding: Modeling the Viasat Cyber Attack with MITRE CTID’s Attack Flow Builder
Introduction
In the complex landscape of modern cybersecurity, understanding the intricate mechanisms of sophisticated cyber attacks has become paramount.
On February 24, 2022, Viasat, a global...
My work about the Viasat attack analysis featured in the Angelina Tsuboi’s course on Satellite Cybersecurity...
I’m very proud and honored to be featured in the Angelina Tsuboi's course on Satellite Cybersecurity Foundations hosted on Udemy. Thank you very much...
The dark side of the DNS or the war of the port 53
I am very happy and proud that my article on DNS security has been accepted and published in the last issue of Hakin9 Magazine...
My cybersecurity review for 2024
What an incredible end to 2024. I’ve had some wonderful experiences. I’ve successfully met many challenges in cybersecurity.
I've had some incredible opportunities and I've...