Introduction
In the complex landscape of modern cybersecurity, understanding the intricate mechanisms of sophisticated cyber attacks has become paramount.
On February 24, 2022, Viasat, a global communications company, fell victim to a significant cyber attack that disrupted satellite internet services across Europe. This incident highlighted the vulnerabilities in critical infrastructure and the need for advanced threat modeling tools.
As part of a previous study, the work of which you can read in this article, I did an analysis of the Viasat cyber attack with the MITRE ATT&CK® framework.
To go further, I conducted in this article, an in-depth analysis of the attack using the Attack Flow Builder, a cutting-edge tool developed by MITRE Engenuity’s Center for Threat-Informed Defense.
About the Viasat hack in brief

The Viasat hack was a cyberattack on American communications company Viasat affecting their KA-SAT network, on 24 February, 2022.
Thousands of Viasat modems got hacked by a « deliberate … cyber event ». Thousands of customers in Europe have been without internet for a month since. During the same time, remote control of 5,800 wind turbines belonging to Enercon in Central Europe was affected.
According to Viasat, the attacker used a poorly configured virtual private network appliance to gain access to the trusted management part of the KA-SAT network. The attackers then issued commands to overwrite part of the flash memory in modems, making them unable to access the network, but not permanently damaged. The satellite itself and its ground infrastructure were not directly affected.
About the Attack Flow Builder Tool
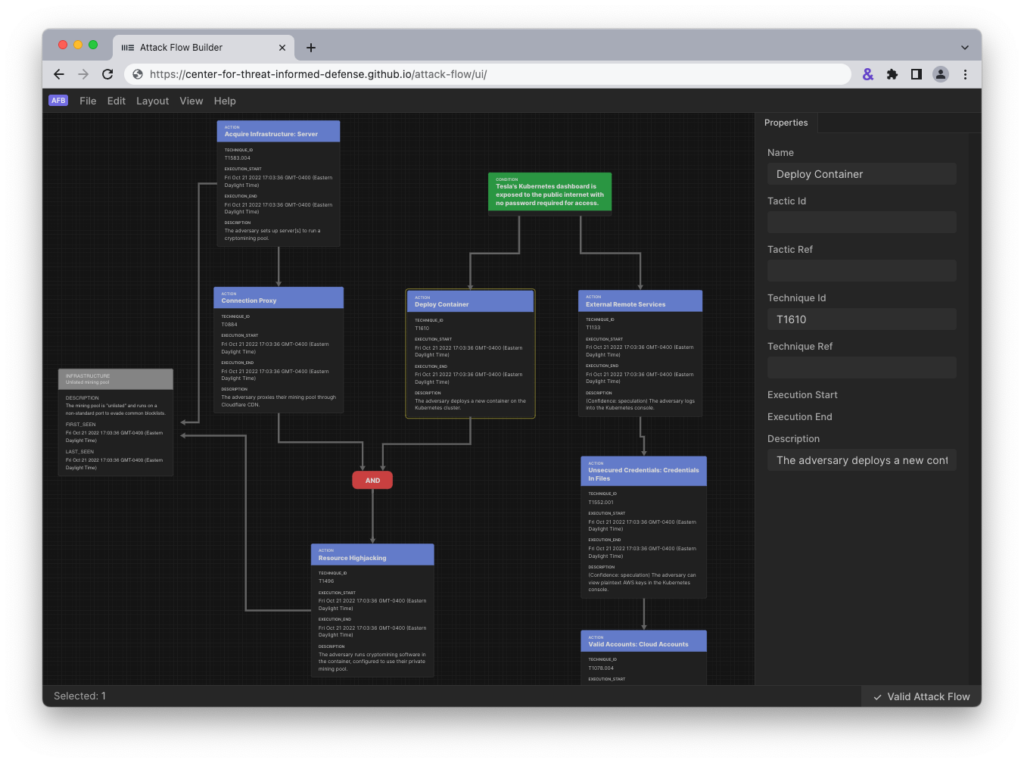
The Attack Flow Builder is an online tool designed by MITRE Engenuity’s Center for Threat-Informed Defense to visualize and analyze complex attack sequences. It allows cybersecurity professionals to model adversary behaviors, providing a comprehensive view of how attackers achieve their objectives.
The key features of the Attack Flow Builder include:
- Visual representation of attack sequences
- Integration with the MITRE ATT&CK framework
- Collaborative sharing capabilities
- Support for various use cases, from threat intelligence to defensive planning
Modeling the Viasat Attack
In my previous work:
- I compared the 4 frameworks that can be used for the space sector: MITRE ATT&CK, SPARTA, SPACE-SHIELD and TREKS.
- I explained why I choose the MITRE ATT&CK Framework
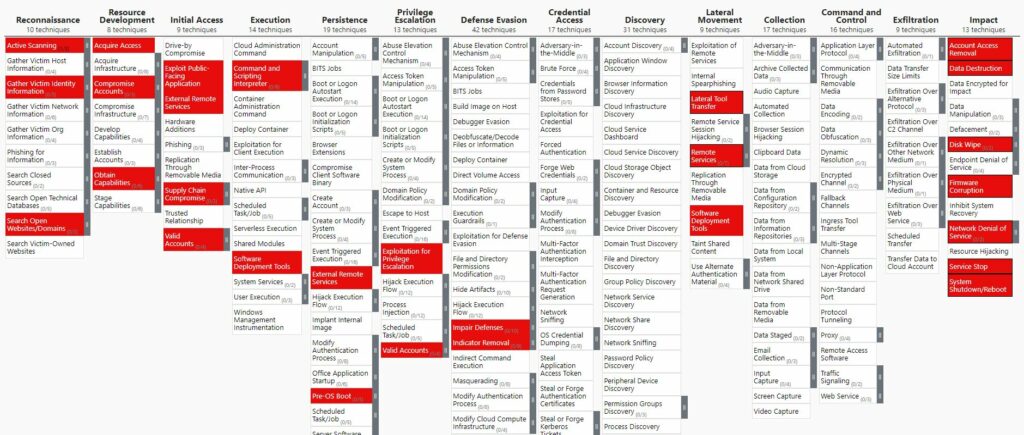
- I identified Tactics, Techniques and Procedures (TTPs) from the MITRE ATT&CK® framework that have been used by the hackers
- I mapped them on the MITRE ATT&CK® Navigator in order to have the complete attack chain.
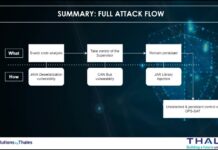
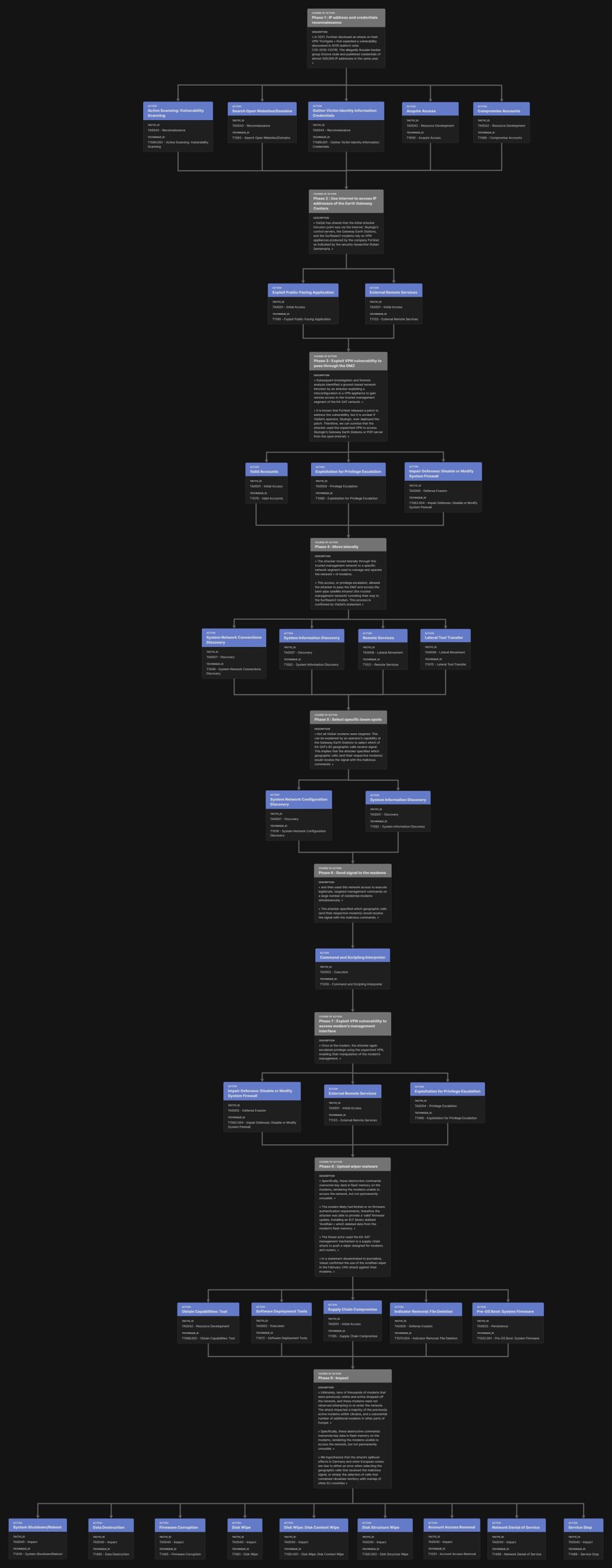
Using results of this work, I created a detailed model of the Viasat cyber attack.
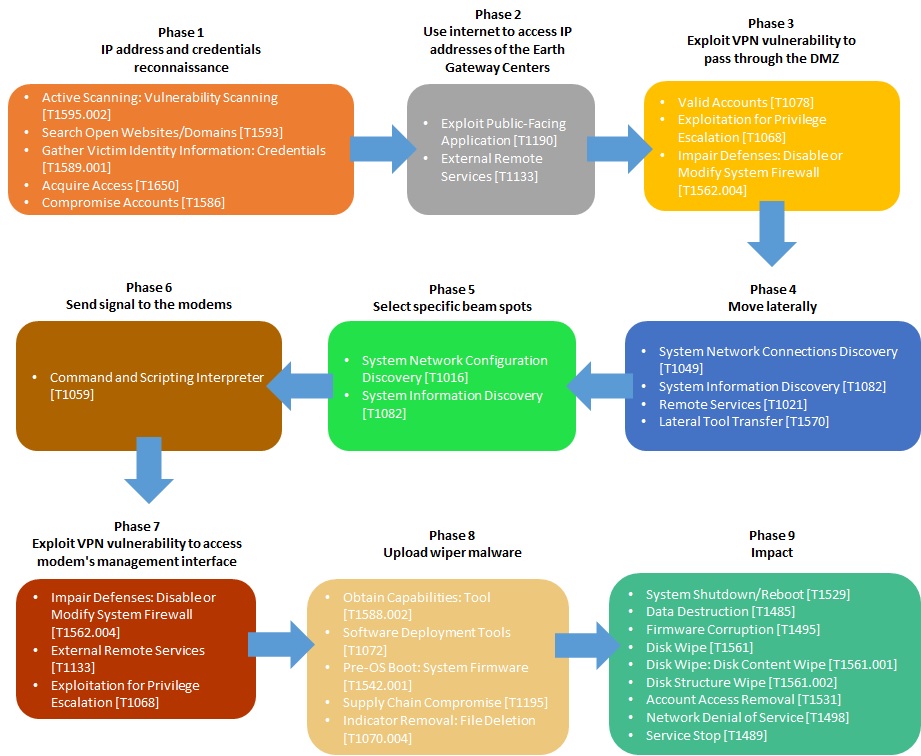
I then utilized the Attack Flow Builder to deconstruct the Viasat cyber attack, meticulously tracing each stage of the intrusion. By systematically documenting the initial access vector, tracking lateral movement within the network, and visualizing the execution of the malicious firmware update, I created a detailed forensic map of the attack’s progression.
Results of the Modeling of the Viasat Attack with the Attack Flow Builder
Original file in big format can be found below
Downloading and sharing the project files
The format used for creating and editing in the Attack Flow Builder is the AFB builder format (.afb). The AFB file below can be used to open the project for further editing in the future.
The machine-readable format for exchanging flows is the JSON format (.json). The JSON file below can be used for exchanging, publishing and processing Attack Flows.
The PNG format is used to save the flow. This format is great for visualizing, using in presentations, sharing with others, etc..
- Download json file of the viasat attack
- Download png file of the viasat attack
- Download afb file of the viasat attack
Benefits of Attack Flow Modeling
The attack flow modeling process revealed critical insights into the attack’s methodology, exposing potential vulnerabilities and attack vectors. This approach allows a better understanding of the specific incident. This approach also provides a replicable framework for analyzing similar complex cyber incidents.
Impact and Perspectives
By demonstrating the Attack Flow Builder’s capabilities, I hope my work will contribute to the broader cybersecurity community’s understanding of threat modeling.
I think that the Attack Flow Builder tool represents a significant step towards more proactive, intelligence-driven defensive strategies, enabling organizations to anticipate and mitigate potential cyber risks more effectively.
My analysis not only illuminates the specifics of this particular Viasat Attack but also provides a methodology for understanding and defending against complex cyber threats in an increasingly interconnected landscape.
In the complex landscape where cyber threats continue to evolve with increasing sophistication, a such threat modeling approach allo to develop robust and adaptive cybersecurity frameworks.
Thank’s for the Center for Threat-Informed Defense for this very useful tool.
The dissemination of my work aims to contribute to the advancement of security practices in the field of satellite systems.
The objective of presenting my work also offers me the opportunity to receive constructive feedback so that I can continue in my research.