Brandon Bailey & Brad Roeher from the SPARTA team analyzed, in this article, Thales Group’s CYSAT ’23 presentation material to deconstruct the experiment, extract lessons learned, and document potential countermeasures.
Summary of the full attack flow
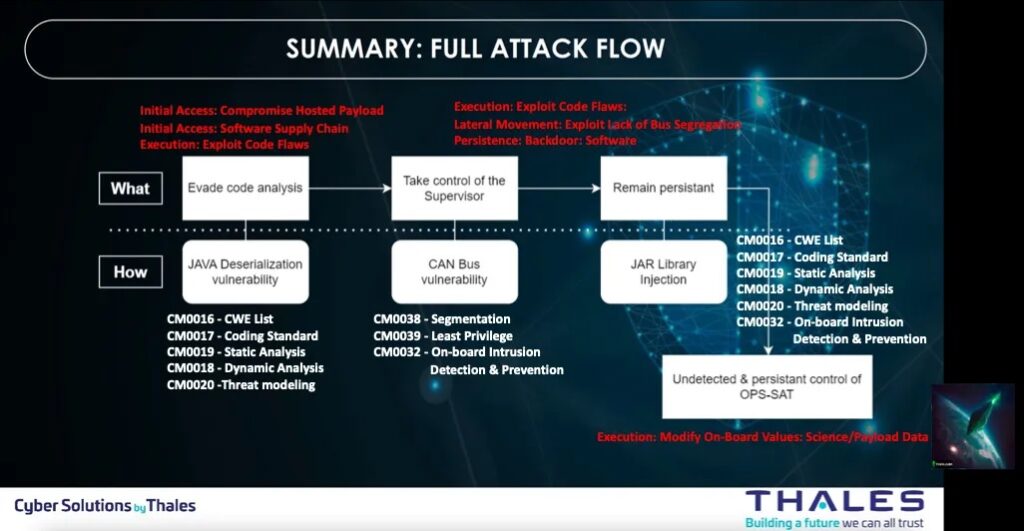
The SPARTA (Space Attack Research and Tactic Analysis) Framework was used to identify the tactics, techniques, and associated countermeasures associated with the experiment/attack.
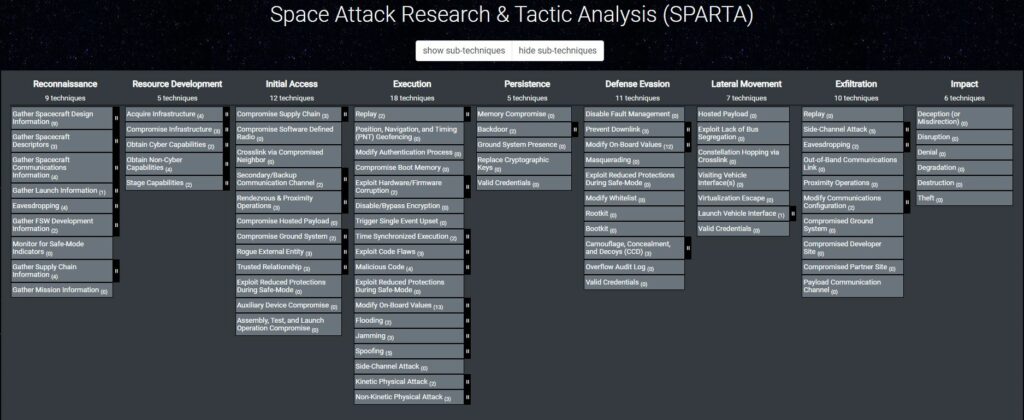
More about the SPARTA Framewok
They utilized the SPARTA Navigator tool to construct the attack chain and generated an Excel export to pinpoint relevant countermeasures. Subsequently, a thorough analysis is conducted to ensure the applicability of the associated countermeasures to the specific Tactics, Techniques, and Procedures (TTPs).
The SPARTA Navigator proves invaluable in presenting a comprehensive array of countermeasures categorized by defense-in-depth, effectively minimizing the risk posed by TTPs. By leveraging the SPARTA Navigator, we successfully map the attack chain to SPARTA TTPs, as exemplified below.
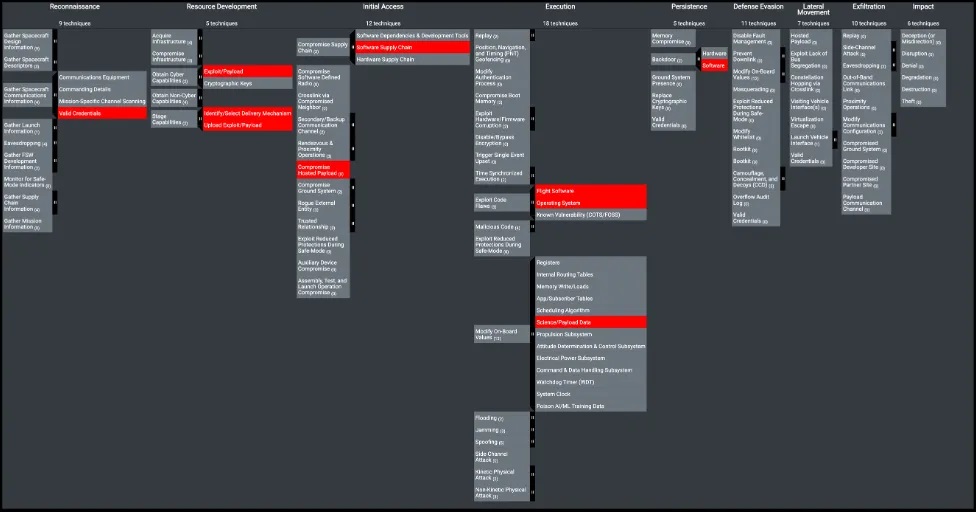
Upon exporting the data from the SPARTA Navigator, they have identified eight countermeasures. Out of these, five pertain to terrestrial countermeasures intended to prevent vulnerable software from infiltrating the spacecraft. The remaining three countermeasures are implemented onboard the spacecraft itself, serving to protect against and/or detect the TTPs executed during the experiment.
More about the analysis of the CYSAT 2023 Demo by SPARTA team
More about the demo
- Thales seizes control of ESA demonstration satellite in first cybersecurity exercise of its kind
- Hacking demo at CYSAT 2023: world first or « déjà vu »
Here is what I know
- Thales demo at CYSAT: what was the point again
Check this demo in video