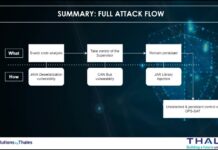
An analysis of the Thales satellite hacking demo at CYSAT 2023 with the MITRE...
Disclaimer
Please be informed that the analysis detailed in this article is entirely separate from the hacking experiment conducted by the Thales team on the...
Enhancing Threat Understanding: Modeling the Viasat Cyber Attack with MITRE CTID’s Attack Flow Builder
Introduction
In the complex landscape of modern cybersecurity, understanding the intricate mechanisms of sophisticated cyber attacks has become paramount.
On February 24, 2022, Viasat, a global...
My work about the Viasat attack analysis featured in the Angelina Tsuboi’s course on Satellite Cybersecurity...
I’m very proud and honored to be featured in the Angelina Tsuboi's course on Satellite Cybersecurity Foundations hosted on Udemy. Thank you very much...
The dark side of the DNS or the war of the port 53
I am very happy and proud that my article on DNS security has been accepted and published in the last issue of Hakin9 Magazine...
My cybersecurity review for 2024
What an incredible end to 2024. I’ve had some wonderful experiences. I’ve successfully met many challenges in cybersecurity.
I've had some incredible opportunities and I've...
My experience and tips after successfully passed the CISM (Certified Information Security Manager) from...
 I'm thrilled to share that I've earned the CISM (Certified Information Security Manager) from ISACA. You can view my achievement on Credly.
I'm thrilled to share that I've earned the CISM (Certified Information Security Manager) from ISACA. You can view my achievement on Credly.
 This...
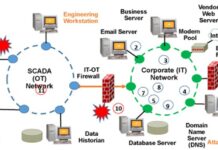
This... How to model an attack on an Industrial Control Systems (ICS)
Attacks on OT (Operational Technology) systems are made easier due to the OT/IT convergence.
The figure below is showing an example of OT/IT convergence.
Attacks on OT...
Space and Satellites Security Conferences at DEF CON 32 (and a little bit Aviation...
The videos from the Def Con 32 conference held in Las Vegas from August 8th to 11th are now online. Perfect for keeping busy...
Very proud to receive the certificate of completion : « Introduction to Cybersecurity in...
I’m very proud to receive the following certificate of completion for having successfully completed the training course : « Introduction to Cybersecurity in Space...
How I used MITRE EMB3D™ Threat Model to identify Siemens PLC vulnerabilities exploited by...
Introduction
In this article, I will show how I used the MITRE EMB3D™ Threat Model to identify vulnerabilities in SIEMENS PLCs that were exploited by...