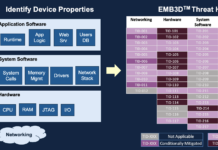
MITRE Releases EMB3D™ – A Cybersecurity Threat Model for Embedded Devices
Collaborative framework provides common understanding to mitigate cyber threats to critical infrastructure
MCLEAN, Va. & BEDFORD, Mass., May 13, 2024--(BUSINESS WIRE)--The EMB3D Threat Model is...
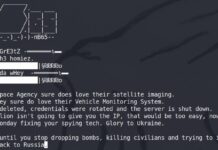
Hacktivism Goes Orbital: Investigating NB65’s Breach of ROSCOSMOS
In March of 2022, Network battalion 65 (NB65), a hacktivist affiliate of Anonymous, publicly asserted its successful breach of ROSCOSMOS’s satellite imaging capabilities in...
“Space Cybersecurity” magazine special edition from PenTest and Hakin9
PenTest and Hakin9 are very proud to present with a special edition, created in a collaborative process between experts in the field of space...
“Introduction to Cybersecurity in Space Systems” with Tim Fowler is coming up during the...
Tim Fowler will provide a training course called "Introduction to Cybersecurity in Space Systems" at "The Most Offensive Con that Ever Offensived – Bypass...
Aerospace cybersecurity manuals bundle : satellites, drones, airplanes, and signals intelligence systems
Angelina Tsuboi is a programmer, mechatronics developer and Engineer, a pilot, a Scientific Researcher and cybersecurity researcher. She is currently working for NASA. She...
« Aerospace Cybersecurity: Satellite Hacking » course review
I just successfully completed the comprehensive course on « Aerospace Cybersecurity: Satellite Hacking » and passed successfully the final exam with a result of...
ethicallyHackingspace (eHs)® h4ck32n4u75™ (Hackernauts) Community Member
I'm very proud to have been choosen as ethicallyHackingspace(eHs)® h4ck32n4u75™ (Hackernauts) Community Member. Thank's to William Ferguson for this distinction.
The "h4ck32n4u75™" badge, pronounced "hackernauts,"...
My cybersecurity review for 2023
What an incredible end to 2023. I've had some wonderful experiences. I've successfully met many challenges in cybersecurity.
I took part of the 3-day...
23 Tips to Pass CCSK (Certificate of Cloud Security Knowledge) from CSA at the...
At the beginning of April 2020, I successfully passed the CCSK certification (Certificate of Cloud Security Knowledge). Now, I give you some tips and...
Top des comptes #Cyber à suivre sur Linkedin
Souvent on pense à Twitter pour réaliser sa veille sécu. Mais Linkedin reste une excellente source d'information dans le domaine du cyber. Je vous...