2nd International Conference on Gravitation, Astrophysics and Cosmology (ICGAC2026) – April 16-18, 2026 in...
We are pleased to announce that the 2nd International Conference on Gravitation, Astrophysics and Cosmology (ICGAC2026) will be held on April 16-18, 2026, in...
An analysis of the Thales satellite hacking demo at CYSAT 2023 with the MITRE...
Disclaimer
Please be informed that the analysis detailed in this article is entirely separate from the hacking experiment conducted by the Thales team on the...
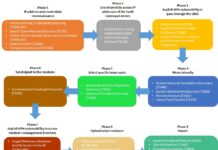
Enhancing Threat Understanding: Modeling the Viasat Cyber Attack with MITRE CTID’s Attack Flow Builder
Introduction
In the complex landscape of modern cybersecurity, understanding the intricate mechanisms of sophisticated cyber attacks has become paramount.
On February 24, 2022, Viasat, a global...
My work about the Viasat attack analysis featured in the Angelina Tsuboi’s course on Satellite Cybersecurity...
I’m very proud and honored to be featured in the Angelina Tsuboi's course on Satellite Cybersecurity Foundations hosted on Udemy. Thank you very much...
My cybersecurity review for 2024
What an incredible end to 2024. I’ve had some wonderful experiences. I’ve successfully met many challenges in cybersecurity.
I've had some incredible opportunities and I've...
My cybersecurity review for 2023
What an incredible end to 2023. I've had some wonderful experiences. I've successfully met many challenges in cybersecurity.
I took part of the 3-day...
[Book] The Battle Beyond: Fighting and Winning the Coming War in Space
Fundamentally, Paul Szymanski and Jerry Drew remind us that--more than just simply a clash of weapons--all warfare manifests as a competition between human minds....
Viasat Attack: A Space Cyber Attack Post Mortem Investigation
Introduction
In this paper, I choose to investigate the Viasat cyber attack that occurred on 24 February, 2022. First, I will summarize the chronology of...
The Interstellar Integrity (i2) magazine interviewed me about my passion for space and cybersecurity
I'm very proud to be featured in the second edition (nov 2023) of Interstellar Integrity (i2) released by ethicallyHackingspace(eHs)®.
Thank's to William Ferguson for this...
My work about the Viasat attack analysis featured at the BSIDES St. Louis 2023 hacking education conference
I'm very proud to be featured by Tim Fowler in his presentation at BSIDES St. Louis 2023 hacking education conference. Tim Fowler is an offensive security analyst at Black...






![[Book] The Battle Beyond: Fighting and Winning the Coming War in Space](https://www.spacesecurity.info/wp-content/uploads/2023/12/The-Battle-Beyond-Fighting-and-Winning-the-Coming-War-in-Space-218x150.jpg)