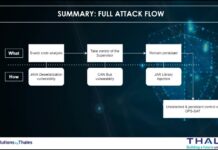
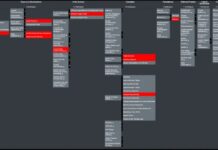
An analysis of the Thales satellite hacking demo at CYSAT 2023 with the MITRE...
Disclaimer
Please be informed that the analysis detailed in this article is entirely separate from the hacking experiment conducted by the Thales team on the...
My cybersecurity review for 2024
What an incredible end to 2024. I’ve had some wonderful experiences. I’ve successfully met many challenges in cybersecurity.
I've had some incredible opportunities and I've...
My cybersecurity review for 2023
What an incredible end to 2023. I've had some wonderful experiences. I've successfully met many challenges in cybersecurity.
I took part of the 3-day...
De qui se MOOC-t-on ? Liste des meilleurs MOOCs sur la Cybersécurité
J'ai découvert, il y a un certain temps, le monde merveilleux des MOOCs. J'ai voulu découvrir de quoi il s'agissait en participant à des...
The Interstellar Integrity (i2) magazine interviewed me about my passion for space and cybersecurity
I'm very proud to be featured in the second edition (nov 2023) of Interstellar Integrity (i2) released by ethicallyHackingspace(eHs)®.
Thank's to William Ferguson for this...
L’Aéro Recrute, un nouveau programme dont je suis Ambassadeur : Pour mettre en avant...
Je suis fier de rejoindre le programme L'Aéro Recrute. Je suis nommé Ambassadeur pour la filière Aéronautique et Spatiale.
A ce titre, vous pouvez me...
My work about the Viasat attack analysis featured in the SIGN.MEDIA #2 newsletter
I’m very proud to be featured by Olga Nasibullina and Tatiana Skydan in THE SIGN.MEDIA #2 newsletter.
Olga Nasibullina works mainly on cybersecurity workforce development,...
My work about the Viasat attack analysis featured at the BSIDES St. Louis 2023 hacking education conference
I'm very proud to be featured by Tim Fowler in his presentation at BSIDES St. Louis 2023 hacking education conference. Tim Fowler is an offensive security analyst at Black...
CyberInflight is part of the contributor list of the SPARTA framework
CyberInflight team is part of the contributor list of the SPARTA framework. The last version published on July 18, 2023, adds more than 60...
Thales confirms its key role to provide cybersecurity for Galileo second generation to meet...
Thales has been notified by the European Space Agency (ESA), on behalf of the European Union Agency for the Space Programme (EUSPA) and the...