Space Odyssey: An Experimental Software Security Analysis of Satellites
The abstact below is taken from a paper written by Johannes Willbold, Moritz Schloegel, Manuel Vogele, Maximilian Gerhardt, Thorsten Holz and Ali Abbasi.
This paper...
ATT&CK v13 released with significant updates : Pseudocode, Swifter Search, Mobile Data Sources and...
🔥 On Tuesday 25 April 2023, the MITRE Corporation released ATT&CK v13, the new version of its framework.
This new version includes significant updates and...
CYSAT ’23, a space cybersecurity conference : Full Keynotes and Presentations
CYSAT ’23 is the first conference in Europe dedicated to satellite and space industry cyber security. It took place from 26 to 27 April...
MITRE Caldera™ for OT enables red teams and blue teams to run automated adversary...
MITRE CALDERA is a framework for automating cyber defense testing. CALDERA is developed by the MITRE Corporation, a nonprofit organization based in the United...
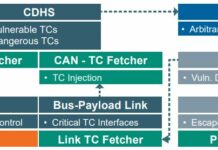
TREKS (Targeting, Reconnaissance, & Exploitation Kill-Chain for Space Vehicles), a new Cybersecurity Framework that...
"The space sector is in need of new frameworks and methodologies specific to our unique operating environment" said Gregory Falco (Aerospace Security & Space...
Hacking demo at CYSAT 2023: world first or “déjà vu”❓ Here is what I know 👇
CYSAT 2023 is over. It’s time to review everything that has happened during this amazing event. But first, let’s remember what CYSAT is.
CYSAT is the leading...
Thales demo at CYSAT: what was the point again
CYSAT 2023 is over. It’s time to review everything that has happened during this amazing event. But first, let’s remember what CYSAT is.
CYSAT is the leading...
Solarium CSC 2.0 has endorsed designation of space systems as a critical infrastructure sector
The Cyberspace Solarium Commission (CSC) was established in the John S. McCain National Defense Authorization Act for Fiscal Year 2019 to "develop a consensus...
Key Takeaways from CYSAT 2023 by Mathieu Bailly, VP at CYSEC and Director of...
CYSAT 2023 is over. It's time to review everything that has happened during this amazing event. But first, let's remember what CYSAT is.
CYSAT is the...
Aerospace Corporation released SPARTA v1.3, a new version of the Space Attack Research and...
Thank's to Calogero Vinciguerra (Space Policy Officer & Space Threats Response Architecture DO at the European External Action Service, EEAS) and Kimberly King (Senior...