An analysis of the Viasat cyber attack with the MITRE ATT&CK® framework
Disclaimer
To do this analysis of the Viasat cyber attack, I used the open-source intelligence (1) of the team composed by Nicolò Boschetti (Cornell University),...
New upcoming course : “Aerospace Cybersecurity: Satellite Hacking” made by Angelina Tsuboi in collaboration...
We are very excited to announce a new upcoming course, "Aerospace Cybersecurity: Satellite Hacking" led by Angelina Tsuboi in collaboration with PenTestMag.
This comprehensive course...
Indiana University – Kelley School of Business launches a new academic program dedicated to...
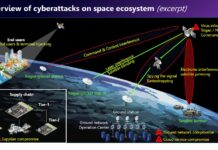
Russia’s cyberattack on ViaSat on the eve of its invasion of Ukraine put the cyber fragility of space systems high on the agenda and...
Thales confirms its key role to provide cybersecurity for Galileo second generation to meet...
Thales has been notified by the European Space Agency (ESA), on behalf of the European Union Agency for the Space Programme (EUSPA) and the...
Coverage by CyberInflight of the Russian satellite telecom Dozor-Teleport Attack
CyberInflight (www.cyberinflight.com) is an independant consulting and business intelligence company dedicated to the topic of Aerospace Cybersecurity. CyberInflight’s goal is to raise the global cybersecurity...
Top 25 most dangerous software weaknesses than can affect satellites in 2023
Issues of vulnerabilities of space systems to cyber attacks has long been ignored for reasons common to industrial systems or SCADA (Supervisory Control And...
Sample of the last Space Cybersecurity Market Intelligence 2023 Report from CyberInflight
CyberInflight and Florent Rizzo shared an excerpt of their last Space Cybersecurity Market Intelligence 2023 Report.
Here is what Florent said in French about this...
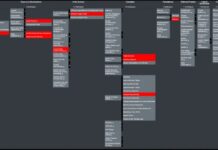
A quick comparaison of recently released Cybersecurity Frameworks for Space Sector
« The space sector is in need of frameworks and methodologies specific to our unique operating environment » said Gregory Falco (Aerospace Security & Space Technology Asst. Prof...
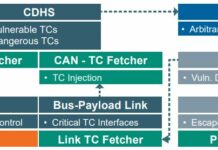
An analysis of the Thales satellite hacking demo CYSAT 2023 by SPARTA team
Brandon Bailey & Brad Roeher from the SPARTA team analyzed, in this article, Thales Group’s CYSAT ’23 presentation material to deconstruct the experiment, extract lessons...
Space Odyssey: An Experimental Software Security Analysis of Satellites
The abstact below is taken from a paper written by Johannes Willbold, Moritz Schloegel, Manuel Vogele, Maximilian Gerhardt, Thorsten Holz and Ali Abbasi.
This paper...