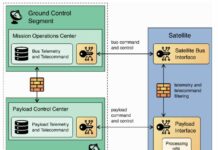
NIST released IR 8401, a new Cybersecurity Framework applied to the ground segment of...
NIST released IR 8401, a new guidance named “Satellite Ground Segment: Applying the Cybersecurity Framework to Assure Satellite Command and Control”.
NIST IR 8401 is...
DEF CON 29 Aerospace Village Videos
DEF CON Aerospace Village is a researcher led, non-profit whose mission is to build a diverse community focussed on the security of everything from...
Space Security Challenge 2021: Hack-A-Sat 2 is back to hack an on-orbit US satellite
The U.S. Air and Space Forces in collaboration with the security research community opened registration May 4 for the qualification round of the second annual Space...
Est-il possible de hacker le lanceur Falcon9 de SpaceX ?
Cet article est traduit en français et publié sur notre site avec l'autorisation de son auteur Téodor Chabin. Vous pouvez retrouvez l'article original ici
Chaque...
Un chercheur alerte sur le risque de piratage des petits satellites comme ceux de...
SpaceX et d'autres sociétés se précipitent pour mettre en orbite des milliers de petits satellites bon marché, mais la pression pour maintenir les coûts...
Des pirates informatiques annoncent avoir infiltré un sous-traitant de la NASA juste après le...
Les opérateurs du rançongiciel (ransomware) DoppelPaymer ont félicité la NASA ainsi que la société SpaceX d'Elon Musk pour le premier lancement d'une fusée privée...
Tous les LIVEs pour suivre en direct le premier lancement d’une fusée SpaceX avec...
Ce soir, mercredi 27 mai 2020, l'histoire va se dérouler sous vos yeux. La NASA et SpaceX lancent les astronautes Robert Behnken et Douglas...
Try to dock the SpaceX Crew Dragon at the space station in this simulator
Put yourself in the shoes of a NASA astronaut and try to dock to the ISS with this Crew Dragon capsule simulator. Will you...
First manned SpaceX Crew Dragon flight set for May 27 liftoff
Barring a last-minute postponement, a SpaceX Crew Dragon capsule will take off from the top of a Falcon 9 rocket on May 27th. The...
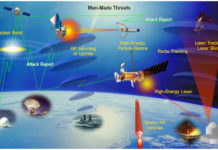
What are the threats to space systems?
In this article, we will try to identify the various threats to space systems.
This article is a synthesis of the CSIS (Center for Strategic...