The Cloud Security Alliance (CSA) is a non-profit organization that focuses on promoting best practices for securing cloud computing environments. It was established in 2008 and has since become a leading authority on cloud security, bringing together industry experts, companies, and government entities to address the challenges and concerns related to security in cloud computing.
The Cloud Security Alliance (CSA) announced the 15th november 2023, the launch of the Certificate of Competence in Zero Trust (CCZT), an authoritative zero-trust training and credential program claimed to be a first in the cybersecurity industry.
In this article, we will describe what the Cloud Security Alliance (CSA) is, then we will go back over the main principles of a Zero Trust Architecture (ZTA) in detail, and finally we will explain what the Certificate of Competence in Zero Trust (CCZT) is.
What is Cloud Security Alliance (CSA)
The primary goals of the Cloud Security Alliance include: Educating and Raising Awareness, Developing Best Practices, Research and Thought Leadership, Certifications and Programs, Collaboration, Advocacy.
The Cloud Security Alliance plays a crucial role in advancing the understanding and implementation of security in cloud computing. By providing resources, best practices, and fostering collaboration, CSA helps organizations navigate the complex landscape of cloud security, ultimately promoting a safer and more secure cloud computing environment for businesses and individuals alike.
What is Zero Trust Architecture (ZTA)
The Zero Trust security model, coined by analyst firm Forrester Research, is a holistic approach to network security that mandates no user or machine should be implicitly trusted, either outside or inside of the network. The concept has evolved as a way to minimize cyber threats and data breaches by not granting automatic trust based on network location.
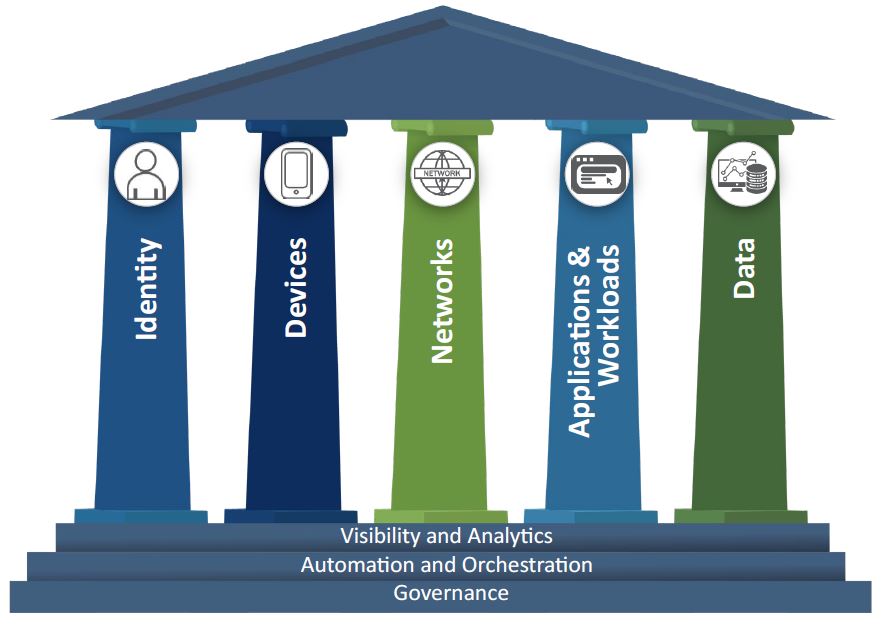
Understanding Zero Trust Principle and Architecture:
Zero Trust operates on the concept “Never Trust, Always Verify”. At its core, it’s designed to protect modern digital environments by leveraging network segmentation, preventing lateral movement, providing Layer 7 threat prevention, and including simplified granular user-access control.
In a Zero Trust architecture, security isn’t treated as a one-size-fits-all model. It aims to eliminate uncontrolled access to resources by assuming that a user, system, or device is potentially compromised, regardless of if they are inside or outside of the security perimeter.
Implementing Zero Trust includes but not limited to: Identify Sensitive Data, Micro-segmentation, Multi-factor Authentication (MFA), Real-time Monitoring and Analytics, User Access Control
Application & Scope:
Zero Trust can be applied to any IT environment, from on-premises data centers to public clouds, and from network to endpoints. This approach is highly effective in protecting users and data in today’s perimeter-less workplaces, where employees, contractors, and partners need to access applications from various locations, networks, and devices.
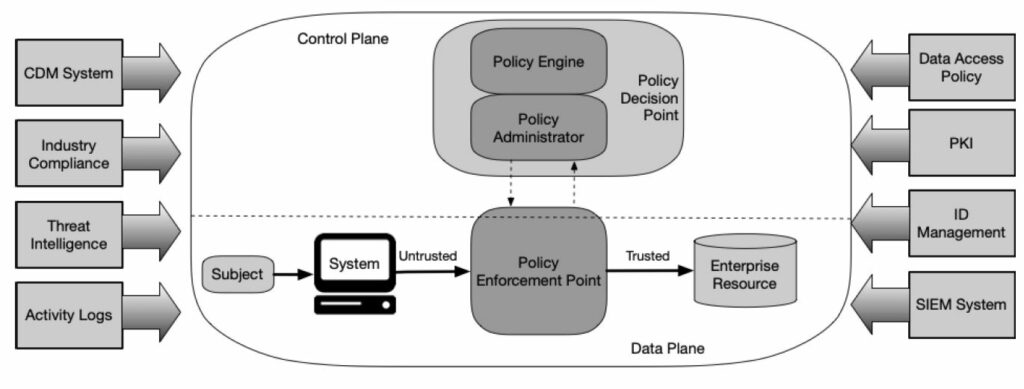
Importance & Future of Zero Trust:
The increasing complexity and fluidity of modern IT environments make traditional perimeter-based security models obsolete. Evolving security threats, remote workforce, digital transformations, cloud adoptions, and complex supply chains led to an increase in the number of digital touch-points that can serve as entry points for sophisticated cyberattacks.
Zero Trust’s focus on securing every access point draws a promising future for IT security. It emphasizes understanding the behavior of network users and devices, thereby enabling early detection and mitigation of potential threats. It offers greater visibility into network activities, lowers the risks of security breaches, and improves compliance by implementing granular data control.
From organizations looking to secure their remote workforces to businesses wanting to lock down their supply chains, Zero Trust is poised to become the new normal for cybersecurity. As entities come to grips with a ‘trust no one’ model, they will be better positioned to tackle the cybersecurity threats of the future.
What is Certificate of Competence in Zero Trust (CCZT)
The Certificate of Competence in Zero Trust (CCZT) is the authoritative Zero Trust training and certificate that delivers the knowledge needed to understand the core concepts of Zero Trust. Developed by CSA, the trusted industry leader for cloud security certificates, the CCZT builds knowledge to drive the definition, implementation and management of Zero Trust over time.
Who is CCZT for?
With Zero Trust established as the future of information security, a Zero Trust based approach will inevitably become a requirement for organizations and a required skill for security professionals. Here are just a few examples of those who should prepare for this inevitability with the CCZT:
- The C-Suite, managers, and decision makers to build a Zero Trust governance and risk posture
- Security engineers, architects, analysts, and administrators to protect devices and build/ automate controls
- Compliance managers to identify the key components of the Zero Trust Governance
Framework and how it supports an organization’s risk and compliance programs
What is the CCZT exam structure?
The CCZT is an open-book, online exam with 60 multiple choice questions covering six core areas of Zero Trust knowledge. Testers have two attempts to complete the exam in the allotted 90-minute timeframe and achieve a minimum passing score of 80%.
What does CCZT cover?
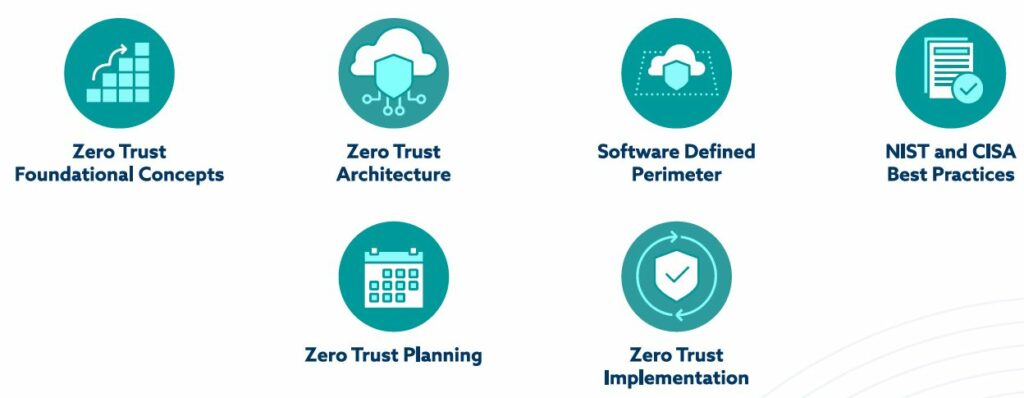
The CCZT evaluates an individual’s knowledge and expertise in these six areas of critical Zero Trust knowledge:
Are there required prerequisites?
There are no prerequisites required for the CCZT, however it is helpful to have your Certificate of Cloud Security Knowledge (CCSK) or a basic understanding of security fundamentals. Completing the ZTT is also highly recommended to prepare for the CCZT.
How do I prepare for the CCZT exam?
There are currently three options to prepare for the exam. Comprehensive CCZT Study Guides are included with the purchase of all CCZT exam tokens.
- Study on your own. Use the free prep-kit to facilitate your independent learning style. The kit includes a CCZT knowledge guide, this FAQ, overview presentation, and authoritative sources to help you prepare.
- Self-paced training online. If you need training flexible enough for your schedule and budget, self-paced online training may be a good fit. The CCZT is based on CSA’s Zero Trust Training (ZTT), an online course that delivers the fundamentals needed to understand the core concepts of Zero Trust covered in the exam.
- Instructor-led training online. This option is good for organizations with tight travel budgets or individuals who prefer a more personal instruction. Learn remotely while still being able to interact with your instructor. Look for a course that fits your schedule.
What is the cost?
The CCZT exam, including study guides, costs $175 and is valid for two years from time of purchase. CCZT instructor-led training with exam and study guides is $1895. The ZTT online course, exam and study guides bundle can be purchased for $455. All listed pricing is confirmed for 2023 only. CSA corporate members qualify for special CCZT pricing and discounts are also available for group training.
Is a digital badge available?
Yes. A CCZT digital badge is issued upon successful completion of the exam. Leverage the CCZT digital badge on your social media channels and resume to showcase your knowledge and validate your expertise.
More infos about CCZT
Check CSA website here