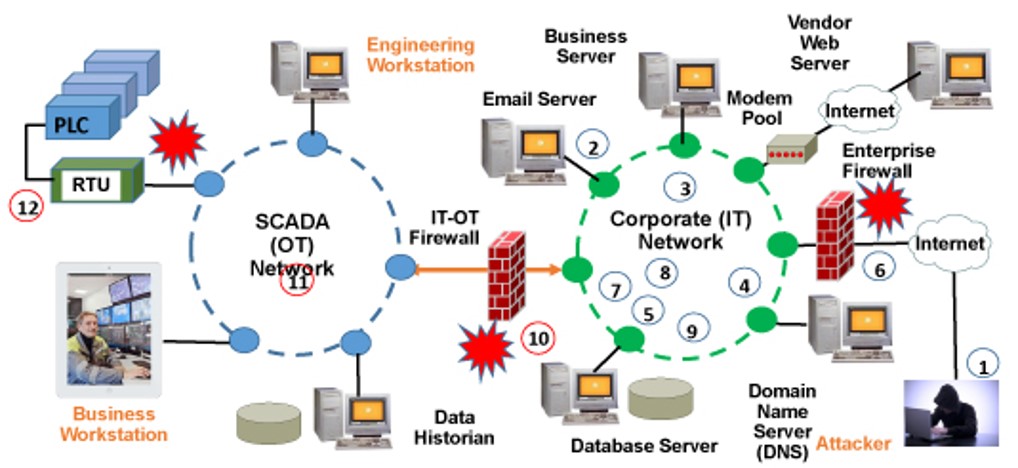
Attacks on OT (Operational Technology) systems are made easier due to the OT/IT convergence.
The figure below is showing an example of OT/IT convergence.
Attacks on OT and ICS systems are modeled by the ICS Cyber Kill Chain and the MITRE ATT&CK for ICS Matrix described below.
ICS Cyber Kill Chain
Published by SANS in 2015 by Michael Assante and Robert M. Lee as an adaptation of the traditional cyber kill chain developed by Lockheed Martin analysts as it applied to ICSs.
The ICS Cyber Kill Chain details the steps an adversary must follow to perform a high‐confidence attack on the ICS process and/or cause physical damage to equipment in a predictable and controllable way.
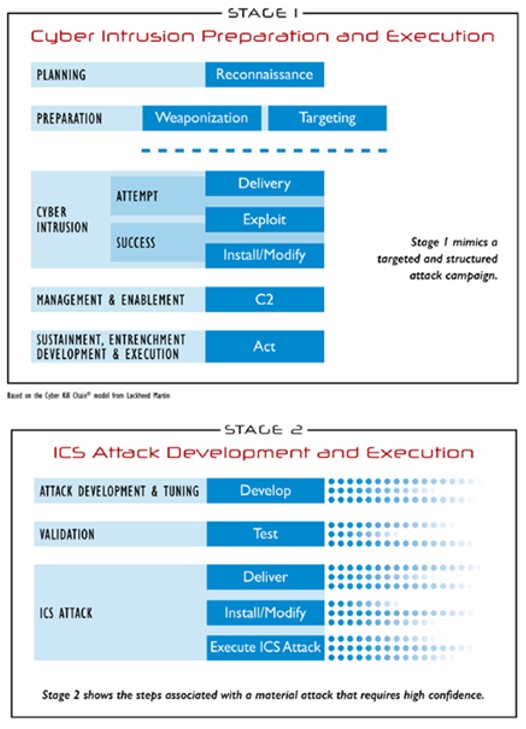
ICS Cyber Kill Chain has Two stages:
- Stage 1 : Cyber Intrusion Preparation and Execution – « IT »
- Stage 2 : ICS Attack Developpement and Execution – « OT »
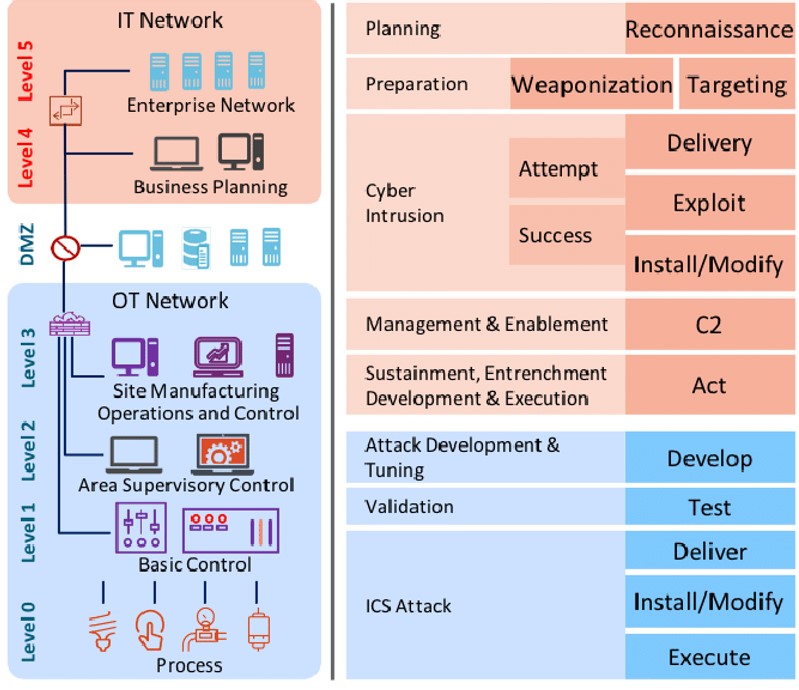
ICS Cyber Kill Chain mapped to the ICS Zoned Architecture
ICS Zoned Architecture (left) : This is the Purdue Model for ICS Security
Cyber Kill Chain for Industrial Control Systems (right) : This is an ICS Attack as Cascading Events
The ICS Cyber Kill Chain is a powerful approach for Neutralizing a Cyber Attack reducing ICS cyber risk. Security Engineering has the challenge to Kill the Kill Chain
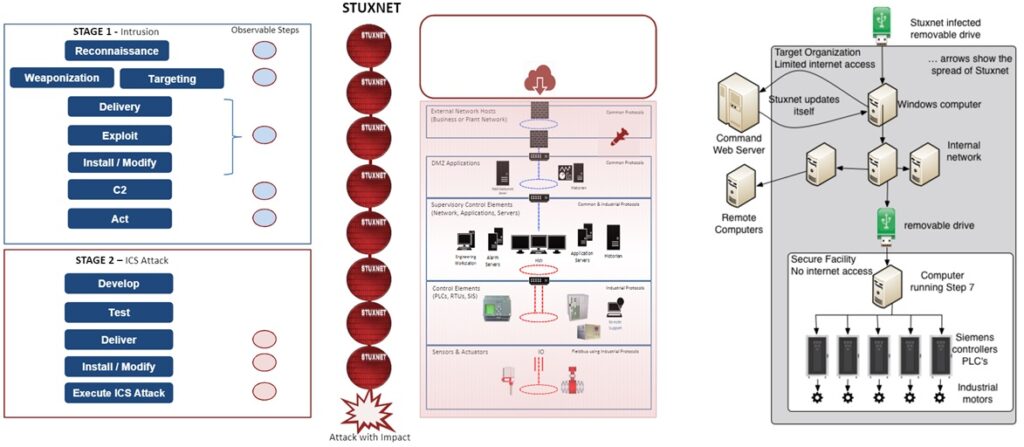
ICS Cyber Kill Chain applied to STUXNET
The figure below is the ICS Cyber Kill Chain applied to STUXNET
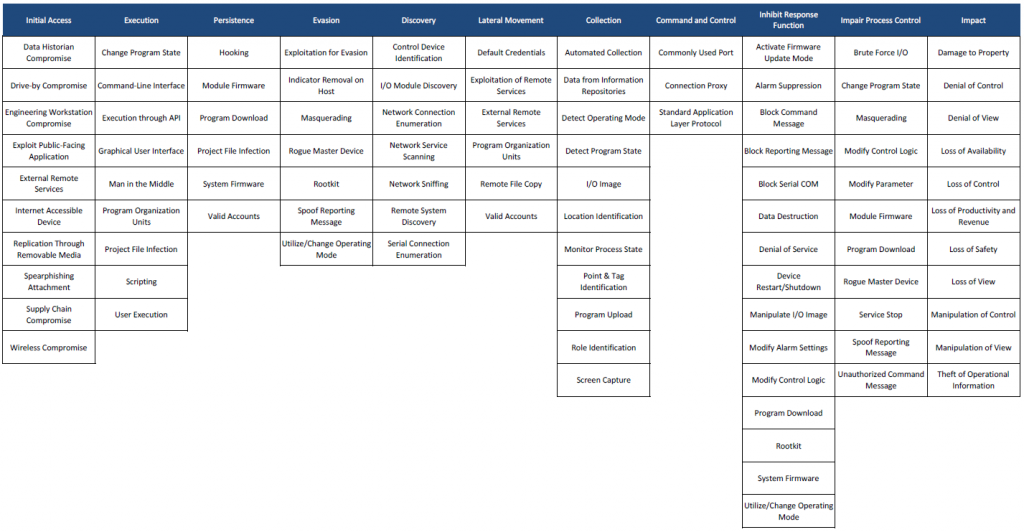
About the MITRE ATT&CK for ICS Matrix
To go futhermore convergence of IT and OT, and the concept of ICS (Industrial Control System), you can also have a look on the MITRE ATT&CK for ICS Matrix.
The MITRE ATT&CK for ICS Matrix is an overview of the tactics and techniques described in the ATT&CK for ICS knowledge base. It visually aligns individual techniques under the tactics in which they can be applied.
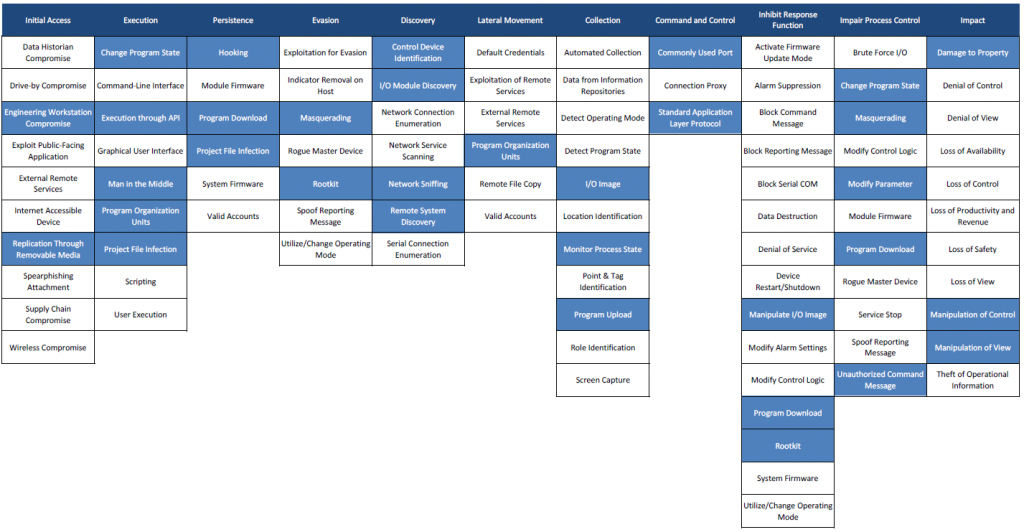
Mapping of Stuxnet attack on the ATT&CK for ICS matrix
Below is the mapping of Stuxnet attack on the ATT&CK for ICS matrix (Than’ks to Airbus Cybersecurity). « Mapping Stuxnet to the ATT&CK for ICS matrix, as shown in figure 3, quickly shows how complex this attack was. Business risk owners can now identify which techniques to focus on if they need to minimise the risk from strikes like Stuxnet. »
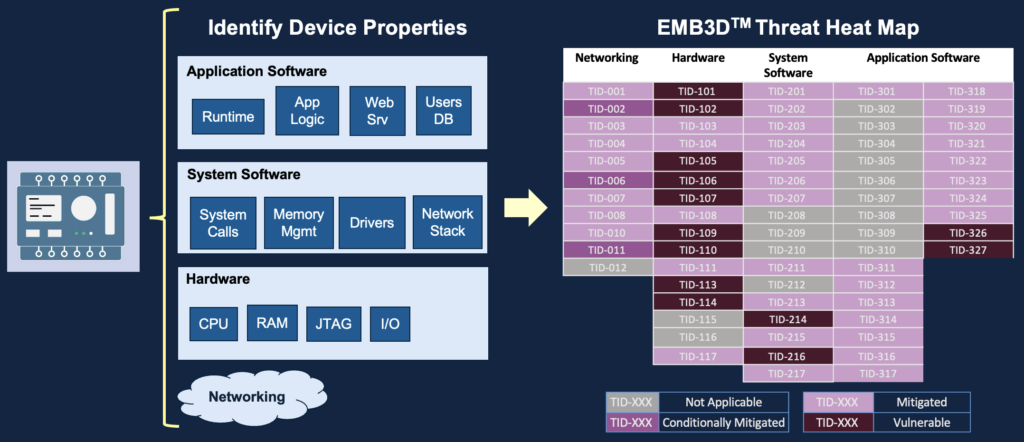
Threat modeling on OT, ICS and embedded systems
MITRE released in May 2024, the EMB3D™ model, a Cybersecurity Threat Model dedicated for Embedded Devices.
EMB3D is aligned with and expands on several existing models, including Common Weakness Enumeration, MITRE ATT&CK®, and Common Vulnerabilities and Exposures, but with a specific embedded-device focus. The threats defined within EMB3D are based on observation of use by threat actors, proof-of-concept and theoretical/conceptual security research publications, and device vulnerability and weakness reports. These threats are mapped to device properties to help users develop and tailor accurate threat models for specific embedded devices.