MITRE CALDERA is a framework for automating cyber defense testing. CALDERA is developed by the MITRE Corporation, a nonprofit organization based in the United States. This framework enables cybersecurity professionals to simulate attacks and defense scenarios in a controlled environment.
CALDERA provides a platform for creating, executing, and analyzing attack campaigns using various tactics, techniques, and procedures (TTPs). It allows users to generate realistic threat scenarios, test their defensive capabilities, and assess the effectiveness of their security measures. The framework supports the emulation of adversary behaviors and can be used for red teaming, threat intelligence analysis, and security tool evaluation. CALDERA aims to enhance organizations’ ability to detect, respond to, and mitigate cyber threats.
MITRE CALDERA is built on the MITRE ATT&CK™ framework and is an active research project at MITRE.
The framework consists of two components:
1. The core system. This is the framework code, including an asynchronous command-and-control (C2) server with a REST API and a web interface.
2. Plugins. These are separate repositories that hang off of the core framework, providing additional functionality. Examples include agents, GUI interfaces, collections of TTPs and more.
MITRE Caldera™ for OT
At the RSA 2023 conference, MITRE released its MITRE Caldera for OT tool, which allows security teams to run automated adversary emulation exercises that are specifically targeted against operational technology (OT).
As MITRE CALDERA is built on the MITRE ATT&CK™ framework, MITRE Caldera for OT is built on the MITRE ATT&CK™ for ICS framework.
“Cybersecurity within critical infrastructure is paramount for national security, the economy, and the safety of the public,” said Mark Bristow, director, Cyber Infrastructure Protection Innovation Center, MITRE.
“OT and industrial control systems (ICS) need innovative security solutions in order to be more resilient against increasing cyber threats. Often, a compliance-based approach has been taken to ICS cybersecurity which ultimately focuses on ‘easy to measure’ security controls like patch levels and password complexity. Instead, MITRE is offering better ways to measure risk and emulate threats that allow us to prioritize which potential scenarios would have the most impact on essential community services,” Bristow continued.
How can ICS/OT organizations know their cyber defenses are robust?
“During the last few years, OT owners and operators have made significant investments to increase their security postures. While these investments are a great step forward, many of these capabilities have not been thoroughly validated to ensure they are working as designed,” added Bristow. “Instead, MITRE Caldera for OT enables security teams to evaluate their cyber defenses against known OT adversaries.”
OT security teams can leverage MITRE Caldera for OT as an automated, preventive tool to examine their OT cyber environment and determine if there are any existing vulnerabilities that adversaries could exploit or gaps in their security architecture.
MITRE Caldera for OT, as part of the MITRE Caldera framework, provides OT-focused plug-ins to enhance red or blue team training, product testing and evaluation, or even measurement against acceptance testing milestones.
Built on the MITRE ATT&CK for ICS framework, MITRE Caldera for OT emulates the attack path and attacker capabilities that are defined either through ATT&CK for ICS or other custom-built plug-ins.
MITRE Caldera for OT Plugins can be found on Github here (coming soon, around mid-May).
Source : businesswire
Time to designate space systems as critical infrastructure
Recently, the Cybersecurity Solarium Commission (Solarium CSC 2.0) has endorsed designation of space systems as a critical infrastructure sector.
The Cyberspace Solarium Commission (CSC) was established in the John S. McCain National Defense Authorization Act for Fiscal Year 2019 to « develop a consensus on a strategic approach to defending the United States in cyberspace against cyber attacks of significant consequences. » The finished report was presented to the public on March 11, 2020. The William M. (Mac) Thornberry National Defense Authorization Act for Fiscal Year 2021 reauthorized the Commission to collect and assess feedback on the analysis and recommendations contained within the final report, review the implementation of the recommendations contained within the final report, and completing the activities originally set forth for the Commission.
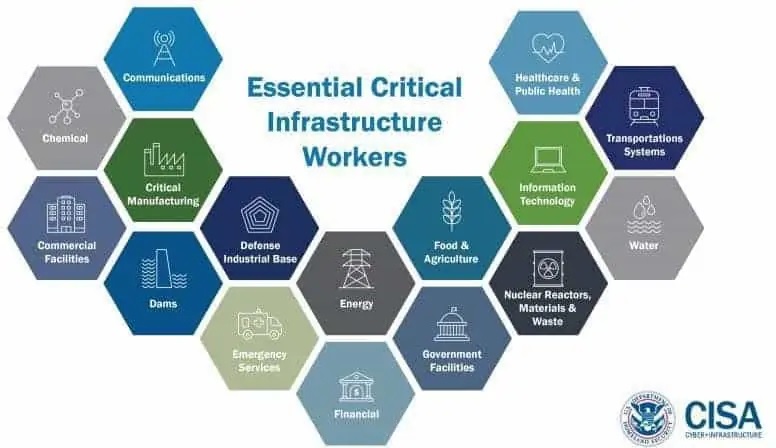
Until today, CISA (Cybersecurity and Infrastructure Security Agency), the US Federal Agency, defined a list of the 16 critical infrastructure sectors.
In the future, space systems will have to be added to this list of critical infrastructure sectors.
We written an article about this announcement here.
Convergence of IT and OT in the Critical Infrastructure Space systems
Space systems can often be seen as a convergence of IT, OT ans ICS in the Critical Infrastructure Space.
That’s why we often use and apply MITRE ATT&CK for ICS framework to identify attack path abd to know how a space system can be attacked.
Need to learn more about MITRE ATT&CK for ICS framework ?
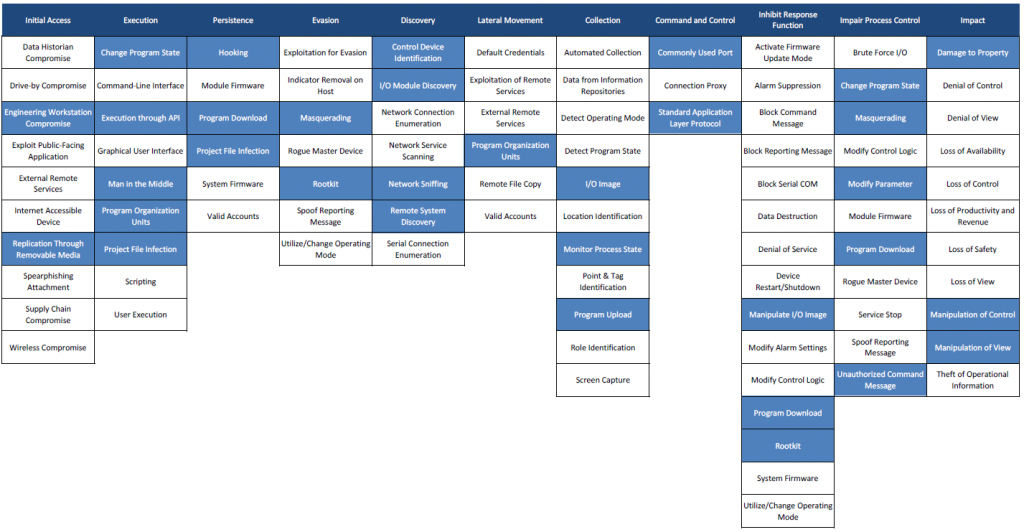
MITRE ATT&CK for ICS framework is the MITRE ATT&CK framework applied on a specific domain.
The MITRE ATT&CK for ICS Matrix is an overview of the tactics and techniques described in the ATT&CK for ICS knowledge base. It visually aligns individual techniques under the tactics in which they can be applied.
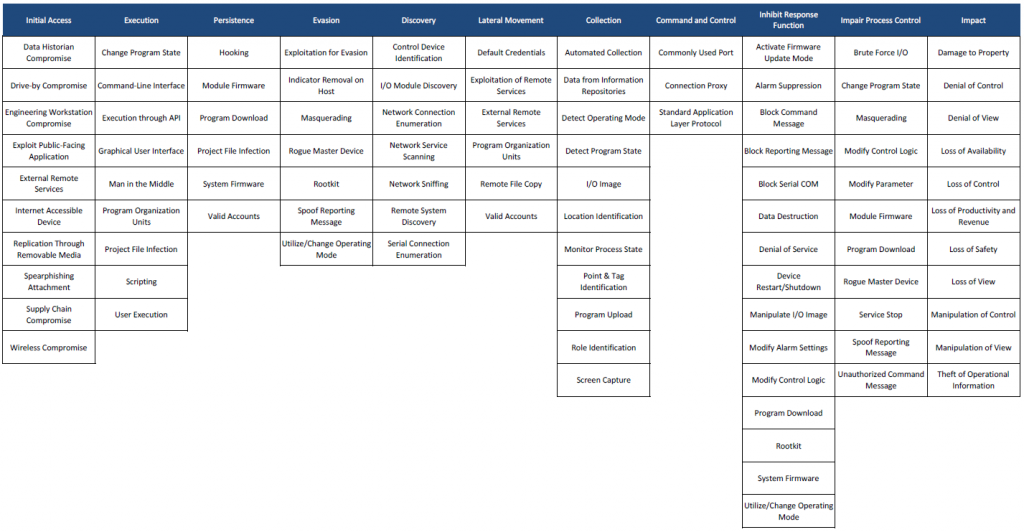
Below is the mapping of Stuxnet attack on the ATT&CK for ICS matrix (Than’ks to Airbus Cybersecurity). « Mapping Stuxnet to the ATT&CK for ICS matrix, as shown in figure 3, quickly shows how complex this attack was. Business risk owners can now identify which techniques to focus on if they need to minimise the risk from strikes like Stuxnet. »