The abstact below is taken from a paper written by Johannes Willbold, Moritz Schloegel, Manuel Vogele, Maximilian Gerhardt, Thorsten Holz and Ali Abbasi.
This paper was presented at the 44th IEEE Symposium on Security and Privacy (S&P) and received a distinguished paper award.
In this paper, they analyze the security of three real-world satellites and discover 13 vulnerabilities that enable attackers take over two of them. They also publish a survey confirms that these are widespread issues.
Terms used in this abstract are : satellites, satellite security, space segment, satellite firmware, threat taxonomy, software security.
The paper can be downloaded here : source 1, source 2, source 3
Abstract — Satellites are an essential aspect of our modern society and have contributed significantly to the way we live today, most notable through modern telecommunications, global positioning, and Earth observation. In recent years, and especially in the wake of the New Space Era, the number of satellite deployments has seen explosive growth. Despite its critical importance, little academic research has been conducted on satellite security and, in particular, on the security of onboard firmware. This lack likely stems from by now outdated assumptions on achieving security by obscurity, effectively preventing meaningful research on satellite firmware.
In this paper, we first provide a taxonomy of threats against satellite firmware. We then conduct an experimental security analysis of three real-world satellite firmware images. We base our analysis on a set of real-world attacker models and find several security-critical vulnerabilities in all analyzed firmware images. The results of our experimental security assessment show that modern in-orbit satellites suffer from different software security vulnerabilities and often a lack of proper access protection mechanisms. They also underline the need to overcome prevailing but obsolete assumptions. To substantiate our observations, we also performed a survey of 19 professional satellite developers to obtain a comprehensive picture of the satellite security landscape.
The figure below is a taxonomy of threats against satellite firmware
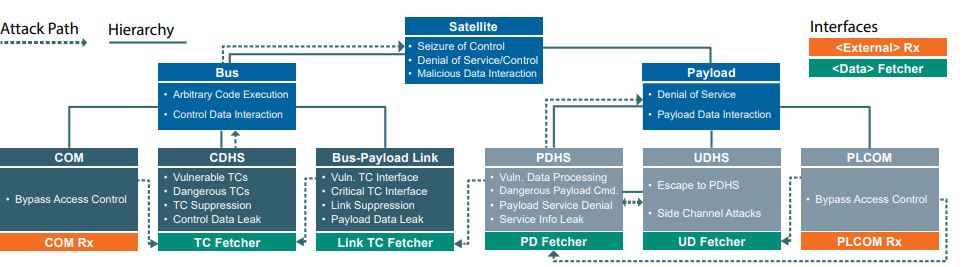
The figure below is a the OPS-SAT threat model
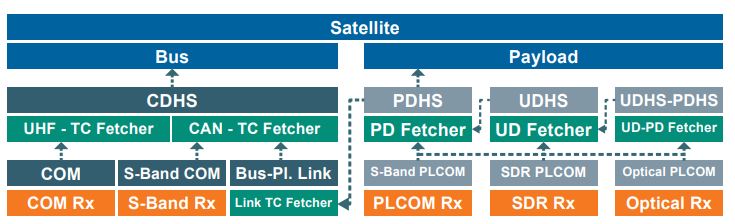
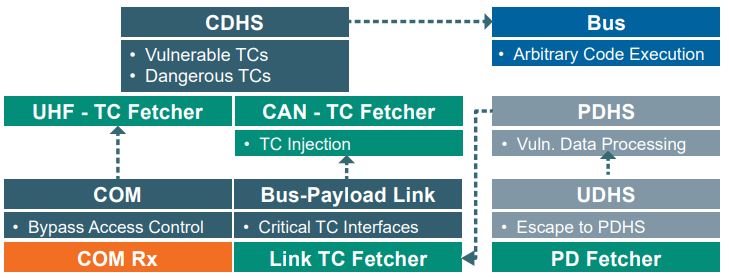
The figure below is an overview of the vulnerabilities identified in the satellite bus and their attacker paths
CISPA researchers have contributed to twelve papers at this year’s. Four of these papers have received the highest honor: A Distinguished Paper Award, given out to the top 1% of submitted papers. Congratulations to everyone involved!