« The space sector is in need of new frameworks and methodologies specific to our unique operating environment » said Gregory Falco (Aerospace Security & Space Technology Asst. Prof at Johns Hopkins, Cybersecurity PhD from MIT).
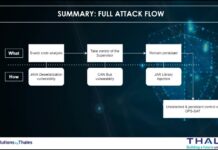
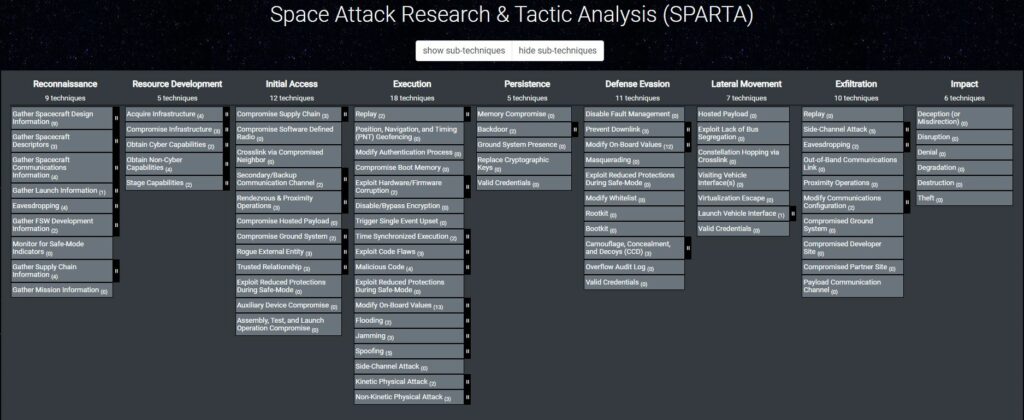
The Aerospace Corporation’s Space Attack Research and Tactic Analysis (SPARTA)
The Aerospace Corporation’s Space Attack Research and Tactic Analysis (SPARTA) framework was already in place. SPARTA is an ATT&CK® like knowledge-base framework but for for Space Missions. SPARTA matrix is intended to provide unclassified information to space professionals about how spacecraft may be compromised due to adversarial actions across the attack lifecycle. You can learn more about SPARTA in our article here.
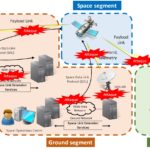
The SPACE-SHIELD (Space Attacks and Countermeasures Engineering Shield) from ESA
There was also the SPACE-SHIELD (Space Attacks and Countermeasures Engineering Shield) from ESA. SPACE-SHIELD is an ATT&CK® like knowledge-base framework for Space Systems. It is a collection of adversary tactics and techniques, and a security tool applicable in the Space environment to strengthen the security level. The matrix covers the Space Segment and communication links, and it does not address specific types of mission. You can learn more about SPACE-SHIELD in our article here.
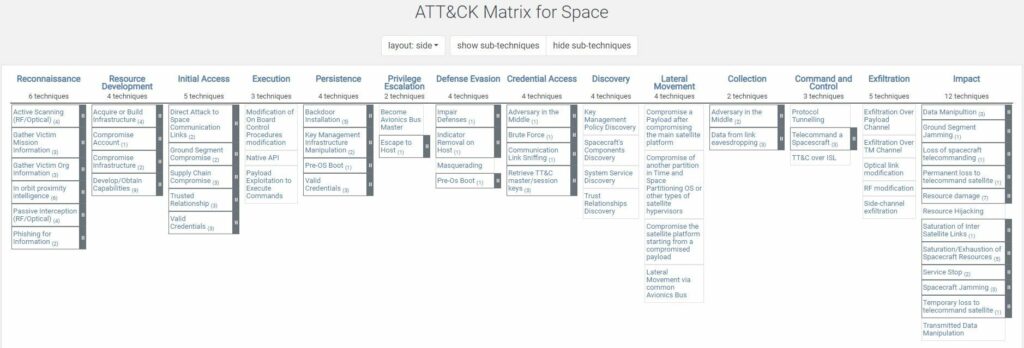
The Targeting, Reconnaissance, & Exploitation Kill-Chain for Space Vehicles (TREKS) Cybersecurity Framework
Now, after more than five years spent researching and working on space system cybersecurity, Dr. Jacob Oakley released the Targeting, Reconnaissance, & Exploitation Kill-Chain for Space Vehicles (TREKS) Cybersecurity Framework.
About Dr. Jacob Oakley
Dr. Jacob Oakley is a cybersecurity professional and author with over 17 years of experience. A foremost expert on offensive cybersecurity, cyber warfare, and space system cybersecurity, he has advised Department of Defense (DoD) and Fortune 500 executives on strategic mitigation of risks and threats to globally distributed, multi-domain network architectures.

The Targeting, Reconnaissance, & Exploitation Kill-Chain for Space Vehicles (TREKS) Cybersecurity framework was developed to provide a taxonomy for understanding, protecting against, and decomposing cybersecurity compromises of space-resident systems, otherwise known as space vehicles (SVs).
TREKS is intended to provide a bridge between the existing frameworks available to address, categorize, taxonomize and analyze cybersecurity compromises of traditional terrestrial based network architectures and the future of cybersecurity for space where those frameworks become more applicable as compromises become more frequent, prolific, and acknowledged. This framework can provide a taxonomy that can be used to characterize foundational aspects of cyber threats to SVs in a way that allows for the identification of trends and enables analysis of this niche target set at the intersection of the space and cyber domains.
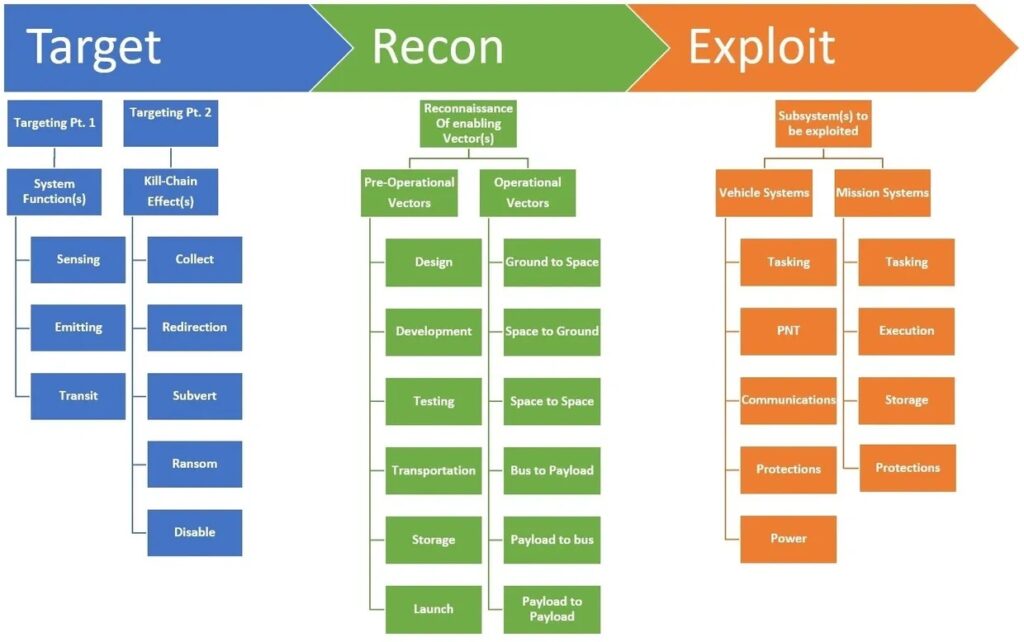
« This framework should be utilized to typify a space vehicle (SV) as a target, based on the function of that SV and an actor’s motivation for targeting it, tying those compromise characteristics to what vectors could be leveraged to exploit subsystems and execute effects related to said motivation. The initial version of this framework could be seen as satellite centric, but the intent is to continuously build out the understandings surrounding this taxonomy to best incorporate all manner of SVs, from satellites to weapons to crewed vessels, labs and beyond. » said Dr. Jacob Oakley.
The TREKS Companion: A Guidebook to the TREKS Cybersecurity Framework
A guidebook is available on the website for free PDF and on Amazon as a kindle or paperback version.
The purpose of this guidebook is to act as a reference to the included TREKS cybersecurity framework and aid in its use by the offensive and defensive cybersecurity communities as well as space system owners and operators.
About future work
This guidebook will continue to be a living document, edited, and updated based on feedback from both the space and cyber communities, with new versions released as appropriate.
As was stated at the beginning of this guidebook, this is intended to be a continuously updated living document to make it easier to leverage and utilize the TREKS cybersecurity framework and act as a mechanism to keep the framework itself up to date.
« Like the Aerospace Corporation’s SPARTA framework contextualizes unique vulnerabilities and countermeasures for the space vehicle, the TREKS framework highlights the unique kill chain for the space vehicle. I encourage Space ISAC and others deep in the weeds of space cyber ops to consider leveraging this » said Gregory Falco.
For usage and licensing information please visit the treksframework.org website.